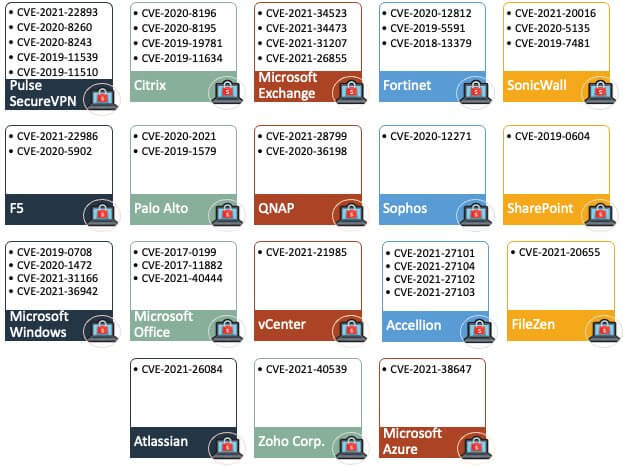
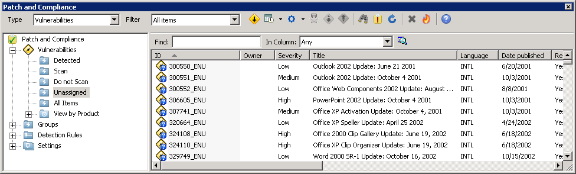
Viewing the security vulnerabilities listing and details - Documentation for BMC Network Automation 8.9 - BMC Documentation

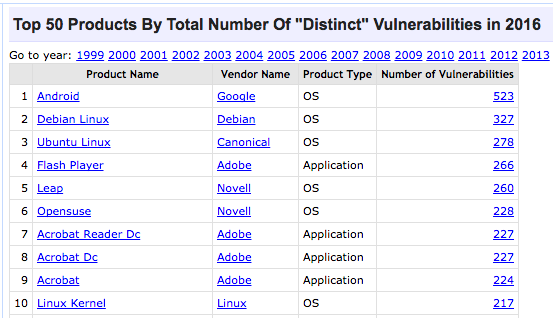
IPA Information-technology Promotion Agency, Japan : IPA/ISEC:Vulnerabilities:CVE (Common Vulnerabilities and Exposures) Overview